In today’s digital world, data is a critical asset for organizations across industries. Protecting sensitive and valuable information is paramount, as data breaches and leaks can lead to severe financial, reputational, and legal consequences. Data Loss Prevention (DLP) solutions are essential cybersecurity tools designed to identify, monitor, and safeguard sensitive data from loss, misuse, or unauthorized access. This comprehensive guide explores the fundamentals of DLP, its importance, threat landscape, and proven strategies and best practices for effective implementation.
What is Data Loss Prevention (DLP)?
Data Loss Prevention (DLP) refers to a set of technologies, policies, and processes aimed at preventing sensitive data from being sent outside an organization’s controlled environment or accessed illegally. It identifies risky or inappropriate sharing, transfer, or use of sensitive data across cloud, on-premises, and endpoint environments. DLP solutions classify data, monitor its movement, and enforce protection policies to prevent accidental or malicious exposure.
DLP forms a central pillar of an organization’s information security (InfoSec) framework and helps maintain compliance with regulations like HIPAA, GDPR, and others by enforcing data governance and protection standards.
How Does DLP Work?
A DLP system leverages a combination of people, processes, and technologies including artificial intelligence (AI), machine learning, and pattern recognition to detect sensitive data activities against predefined security policies. Key functionalities include:
- Data Identification and Classification: Recognizes sensitive data by type (e.g., personal information, payment data, intellectual property) across various repositories.
- Monitoring Data Movement: Tracks data transfers across networks, cloud services, endpoints, and removable media.
- Policy Enforcement: Implements protective controls such as encryption, access restrictions, and alerts to prevent unauthorized sharing or data leaks.
- Incident Response: Provides mechanisms to investigate and remediate violations or breaches swiftly.
DLP policies define what constitutes sensitive information and specify rules for handling it safely, minimizing exposure risk.
Types of Data Threats Addressed by DLP
Understanding the common threats to sensitive data helps organizations tailor their DLP strategies effectively:
- Cyberattacks: Malicious attempts like ransomware, denial-of-service attacks, or spyware target systems to steal, encrypt, or destroy data.
- Malware: Infected files or email attachments can enable unauthorized access, causing widespread disruption and data leakage.
- Insider Risks: Employees, contractors, or partners misusing authorized access either intentionally or unintentionally pose significant threats.
- Unintentional Exposure: Accidental sharing or uploading of sensitive information by employees can lead to compromise.
- Phishing: Deceptive emails trick users into divulging credentials or sensitive data, often leading to breaches.
- Ransomware: Specialized malware that locks critical data and demands payment, leveraging human weaknesses and network vulnerabilities.
DLP works in tandem with identity and access management (IAM), endpoint security, and network defenses to offer holistic protection.
Why is DLP Important?
Organizations face escalating compliance requirements and cyber risks. DLP not only shields data against leaks and breaches but also:
- Enhances visibility into data use and movement.
- Enables compliance with data protection laws by enforcing governance and retention policies.
- Reduces risk exposure from insider threats and external attackers.
- Protects critical data across a dynamic, hybrid environment, including cloud and mobile endpoints.
- Supports incident response and recovery efforts by providing actionable alerts and audit trails.
Integrating DLP into an organization’s cybersecurity strategy elevates its defense posture and trustworthiness with customers and partners.

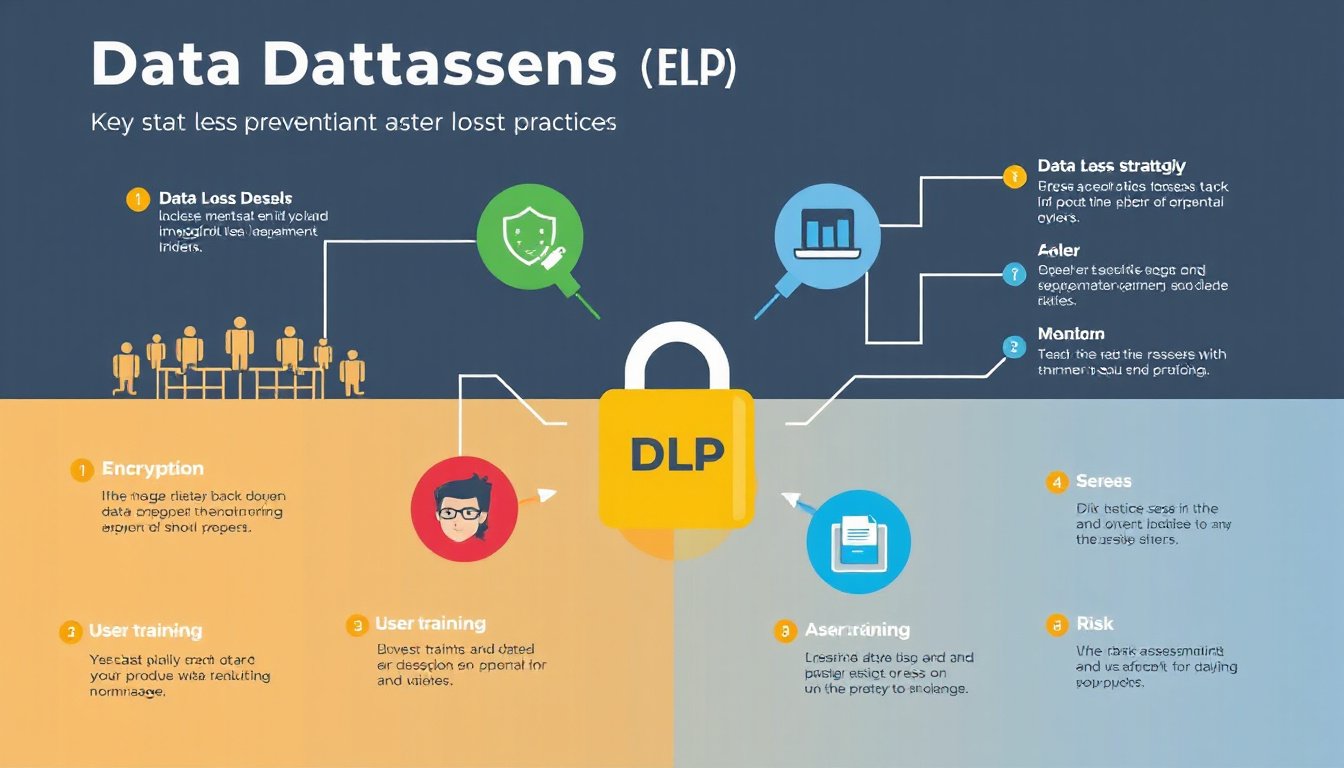
DLP Strategies and Best Practices
Implementing DLP successfully requires a balanced approach combining technology, training, and governance:
1. Know Your Data Landscape
- Conduct data discovery and classification to map sensitive information across all storage and transmission points.
- Develop a taxonomy that tags data by sensitivity level to tailor protection measures effectively.
2. Develop Clear and Enforceable Policies
- Define what constitutes sensitive data and authorized usage clearly.
- Use automated tools to enforce policies consistently to avoid both over-blocking (which hinders productivity) and under-protection.
3. Leverage a Multi-Layered Defense
- Integrate DLP with cloud security, endpoint protection, encryption, and IAM tools for comprehensive coverage.
- Employ AI to detect complex or evolving threats beyond signature-based detection.
4. Educate Employees and Stakeholders
- Conduct regular training to raise awareness about data handling rules, phishing risks, and the importance of compliance.
- Encourage responsible data use and establish clear reporting channels for incidents.
5. Monitor Continuously and Respond Quickly
- Set up real-time monitoring and alerts for suspicious activities.
- Have an incident response plan including containment, remediation, and reporting procedures to mitigate damage swiftly.
6. Ensure Compliance and Audit Readiness
- Maintain detailed logs and audit trails for DLP activities.
- Periodically review and update DLP policies to reflect regulatory or business changes.
Choosing the Right DLP Solution
Modern DLP platforms offer a range of features tailored for different organizational needs:
- Comprehensive Coverage across cloud, endpoint, and network.
- Policy Customization and Automation for flexible, scalable management.
- Integration Capabilities with existing security and compliance tools.
- User-Friendly Interfaces for clear visibility and control.
- Advanced Detection using AI and machine learning for identifying sophisticated threats.
Leading vendors like Microsoft Purview and Fortinet provide enterprise-grade DLP solutions embedded in broader security ecosystems, facilitating unified management.
Conclusion
Data Loss Prevention is a critical component of any robust cybersecurity and data governance strategy. By understanding the principles behind DLP, recognizing the vast array of data threats, and applying strategic best practices, organizations can significantly reduce the risk of sensitive data exposure. Effective DLP empowers businesses to safeguard their most valuable digital assets, ensure regulatory compliance, and maintain customer trust in an increasingly complex threat landscape.
In summary, unlocking the power of DLP means implementing a well-rounded program built on strong policy, intelligent technology, ongoing education, and vigilant monitoring. This synergy ensures sensitive data remains protected wherever it lives or travels within the enterprise environment.